FAQ
The program automatically detects the USB device for its stability. If the flash drive is defined as unstable, then in this case the serial number will be highlighted in red, and all buttons, except for saving registration data and the close button, will be blocked. The key input field will also be blocked and a message will appear in it: “Error USB flash memory.“
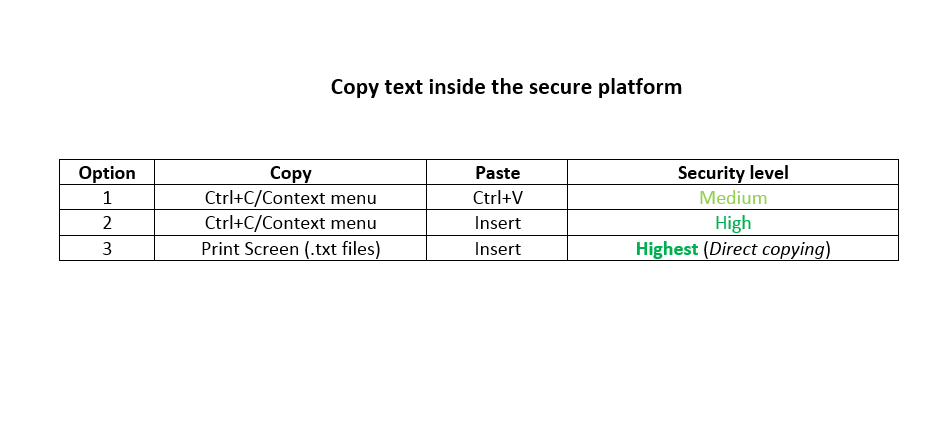
You can copy text inside the secure platform in three ways: Ctrl+C combination, using the context menu (right mouse button) and the programmed Print Screen key. You can paste the text with the usual combination of Ctrl+V and the programmed Insert key.
The difference between these methods lies in the different levels of security of the information being copied (the contents of the clipboard).
The combination of Print Screen and Insert is the safest way, because it allows direct copying from one place (application) to another. However, it allows you to transfer only unformatted text that is used in Notepad and WordPad applications (.txt files). We recommend this combination to transfer logins and passwords.
In new versions, developers of Firefox and Tor Browser have added multiprocessor mode for processing pages and bookmarks. In their opinion, this should speed up the work of the browser. But, after the browser is launched inside the platform, additional processes are launched outside of it and can not communicate with their main process. Therefore, there are problems appeared. To resolve this problem, you should disable multiprocessor mode with the following actions:
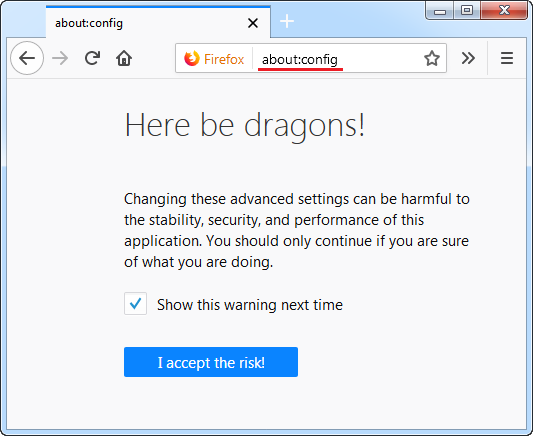
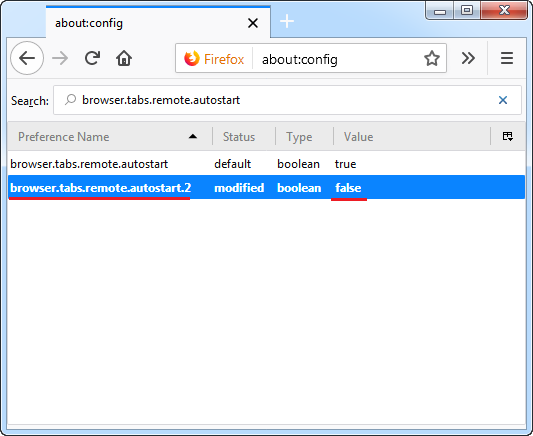
1. Enter “about: config” in the browser bar, press “Enter” and confirm your action.
2. In the window that opens, enter the name of the command “browser.tabs.remote.autostart”. By default the value is set on “true”
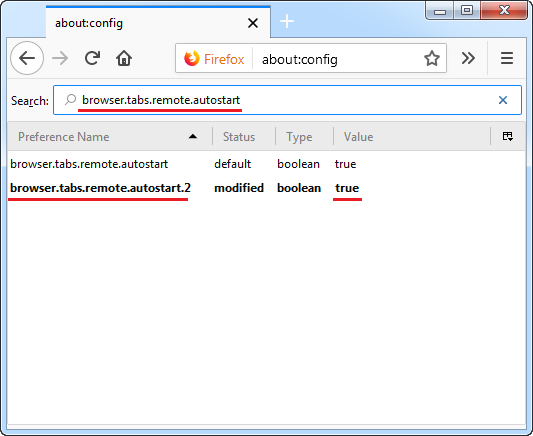
3. Double click on it and the value will change to “false”
After restarting the browser, multiprocessor mode will be disabled and the browser will work correctly in a protected environment. To enable this multiprocessor mode, the entire procedure should be performed in the reverse order.
Registration of COVERT Pro tied to a particular computer or flash drive. Transferring the program is impossible. After you reinstall Windows or format the flash drive the registration data will be destroyed and, according to the license agreement, you must buy a new registration key.
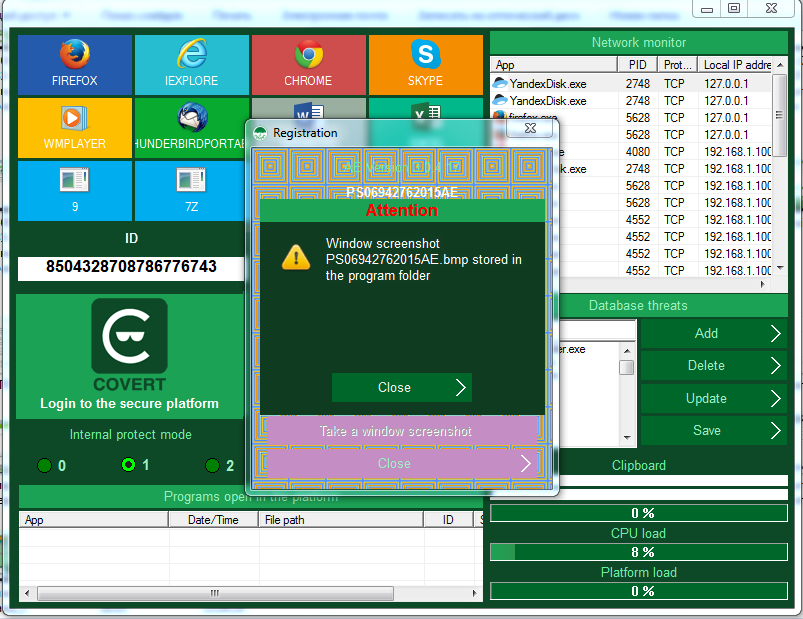
In order to save the registration data there is a function of insurance against unforeseen circumstances described above. It works as follows: before reinstalling the operating system, or formating the flash drive, you need to take a snapshot of the registration window. In versions x.x.x.20 or older snapshot file of the registration window is created automatically, immediately after registering, and saved in the program folder.
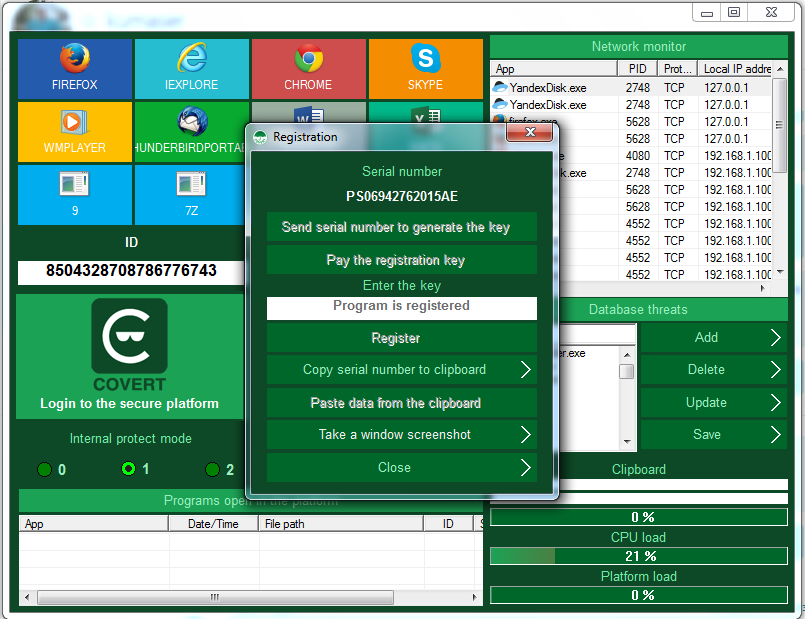
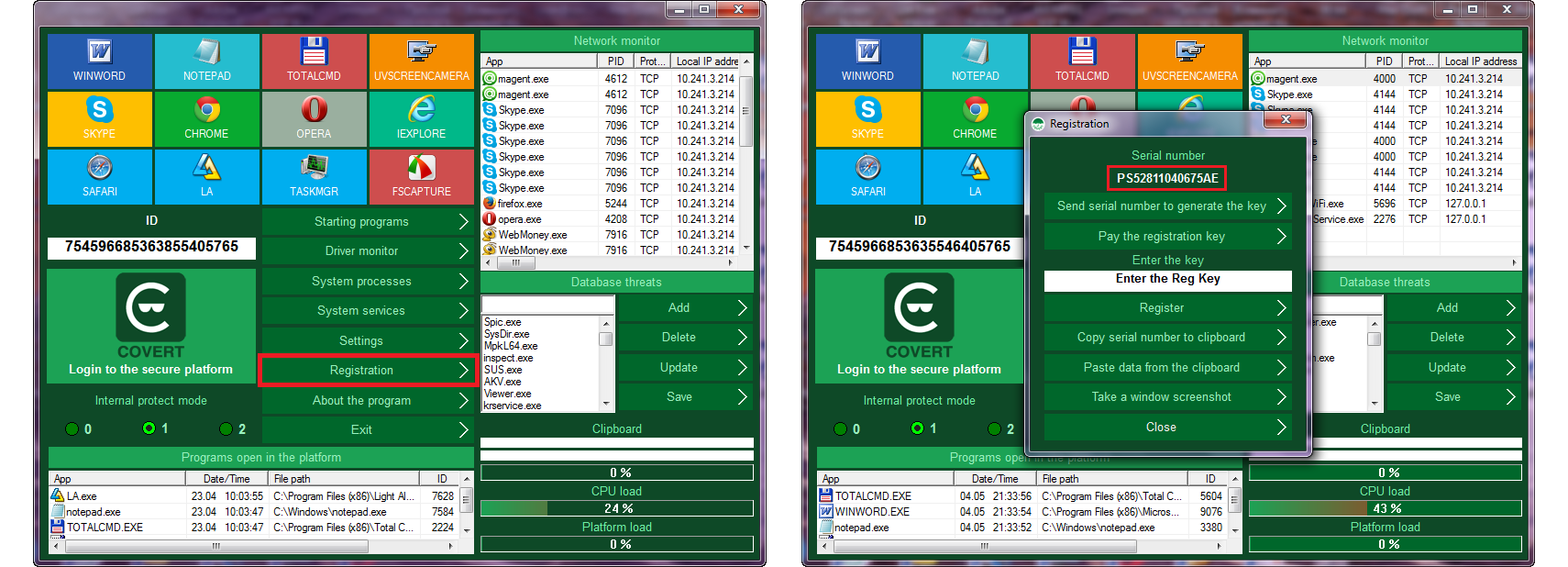
To take a snapshot, click on the “Register” button and you’ll get the registration window.
Then click on the button “Take a screenshot” or “Save registration data” (in the latest version).
The picture will look like this:
The screenshot should be sent to the address support@covert-pro.com.
After reinstalling the operating system or formating the flash drive you should download the installer of the same version from the page https://covert-pro.com/products/.
Once installed on a computer or flash drive, repeat all steps with a screenshot. The serial number will be different. The support service will compare two pictures. If you installed the new version on the same computer or flash drive, you will get a new registration key free of charge.
The login ID is a numeric combination accompanying each occurrence of the user in the masking platform, protecting against external impacts of active malware. Each time the user enters any combination of numbers, either add to or diminish the numbers valid identifier that was previously entered.
Yes. You can update any previously registered version on the same version of software free of charge.
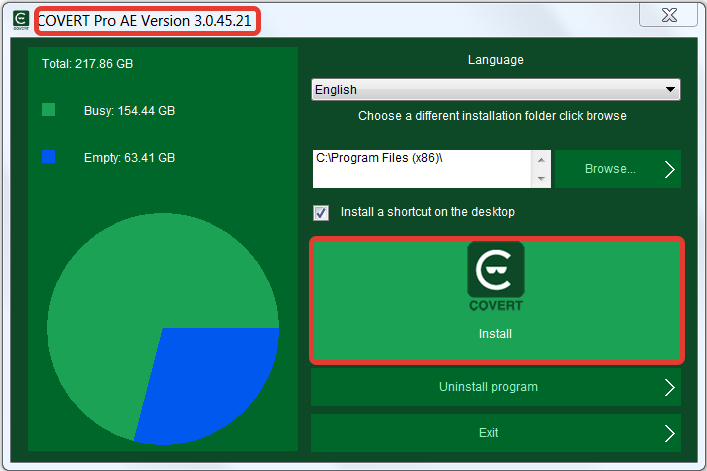
The version number of the program you can see if you click on button “About the program” in the main application window:
To upgrade without loss of registration, do the following:
1. Download the latest version. For example, if you have registered COVERT Pro, then you have to download the same version. If you update a different version of the program, the previous registration will not work.
2. For version COVERT Pro. In the installer, click “Install”. Before installing the new version, it is not necessary uninstall the previous one. Replacement happens automatically.
3. For version COVERT Pro USB. Free upgrade is possible for the flash drive on which had been installed registered version only. Do not delete a folder with a previous program. Then, after the update, you will not have to enter a registration key again. If you did remove the program before the update, find the key and enter it again.
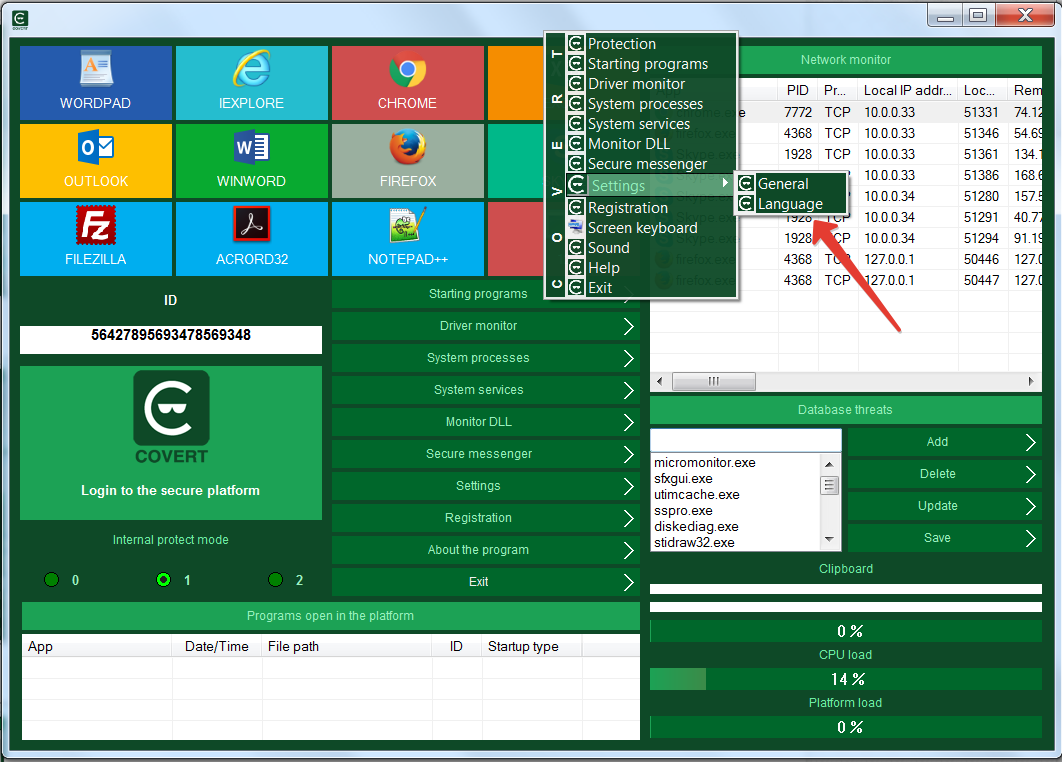
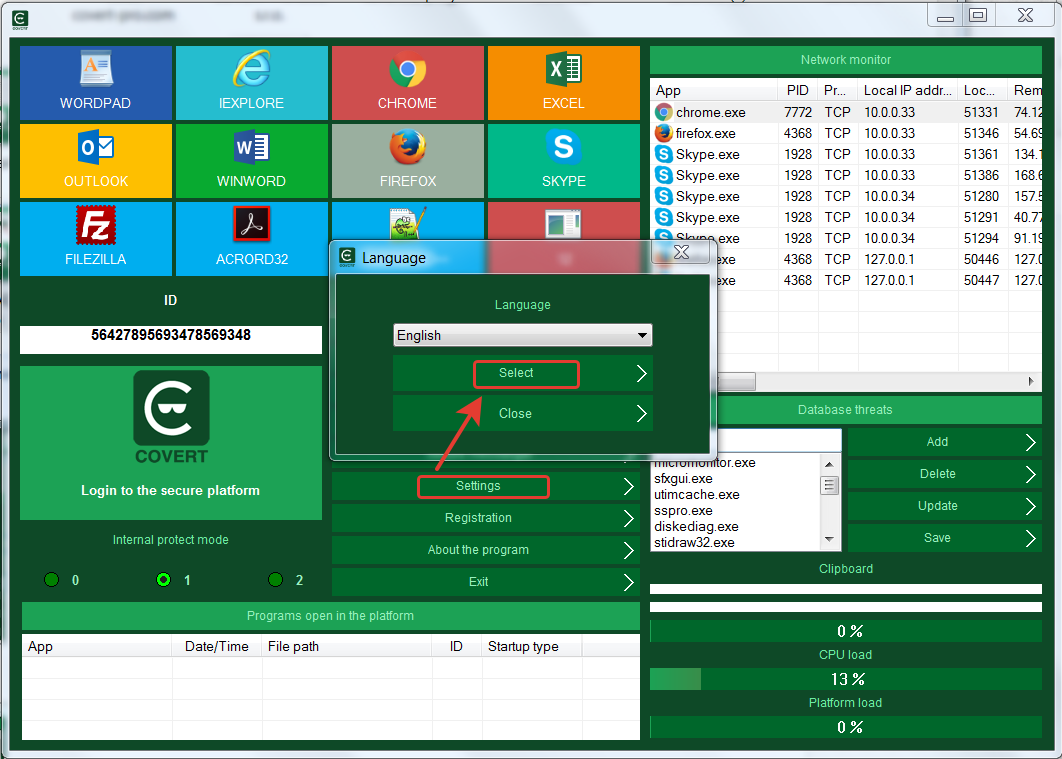
To do this, move the cursor to the upper border of the window (the level with the buttons for minimizing and closing the program) and click the right mouse button. In the menu that appears, select “Settings” and then “Language”.
Another way to change the language is to click on the button “Settings” and then “Language”.
You should not. The demo version is used to try the program COVERT. In the unregistered version, you can see what drivers are installed in the operating system, as well as service and system processes. It allows you to run in a secure platform only one application Notepad and verify protection against spyware. To enter the platform and launch Notepad you must click on the square with the logo of the program. The life of the demo version is not limited.
In the Driver monitor highlighted in green the names of the drivers and their location in the system which belong to the system or approved by the developer. Also highlighted in green driver, which approved by the user. If drivers are highlighted in yellow that they are not in permitted base and are not belong to the system.
If drivers are highlighted in red that they do not exist in the system, but they have an address, or they hide themselves in the system, or they are included in the forbidden database.
In the first mode, the sound of electric shocker sends a signal to the user that the inside of the platform a program was launched not by the user. In the second mode programs that running not by user are blocked. Therefore, an alarm sounds in the form of clicks, which means these programs are being blocked.
There are programs that run at startup its additional copy in a regular mode. Internet Explorer is one of them. COVERT blocks execution copy of the program. To avoid this, switch program in the first or zero protection mode before start IE. After Internet Explorer is running (and its additional copy), you can go to the second security mode.