How data is intercepted from the system clipboard
Most of the users regularly make operations with the system clipboard – copying, cutting and pasting information to transfer it from one application to another. The clipboard is running in the background, and we do not realize that we are using it, like other programs of operating system. However it often contains our confidential information, which we do not want to share with others.
Many people believe that antiviruses protect against all threats, but this is not true.
What is a system clipboard, and who has access to it?
The system clipboard is an area in memory provided by the operating system for temporary storage of data.
Any program running on the computer is able to get access to it, not only those applications between which you transfer data by copying and pasting. This is a legitimate operation which is not prohibited by information protection tools.
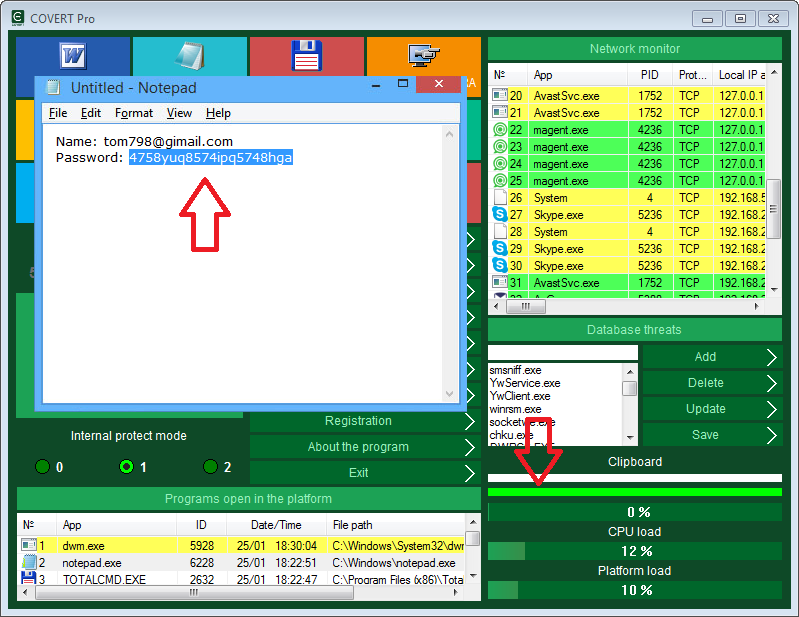
There is a clipboard monitor in COVERT Pro that allows you to see all applications that receive or intercept data from the clipboard, and the function of direct copying and pasting provides you protection of your confidential information from interception.
Open the context menu by clicking right mouse button on the top frame of the menu window. Select the item “Clipboard Monitor“.

The window of monitor consists of two dynamic lists with the following columns: “No. – serial number in the list, “File Name“, “ID” – a unique number of the process in the operating system, “Time” at which the request was sent, “Address” at which the program is located.
The left list shows the application that is the first in the queue to view the clipboard data when its contents change. The operating system creates a queue for requests from applications, and when there is a change in the state of the clipboard (when the user copying any data), information about this spreads to all participants in sequence. To see the next process in the queue for the clipboard data, you should finish previous one using context menu of the list. Using this method you can see all applications that track the changes in the clipboard.
On the screenshot below you can see that after finishing of the first process – punto.exe that belongs to the Punto Switcher application that were waiting for data from the clipboard, another process is appeared – VirtualBox.exe (program for virtualization).
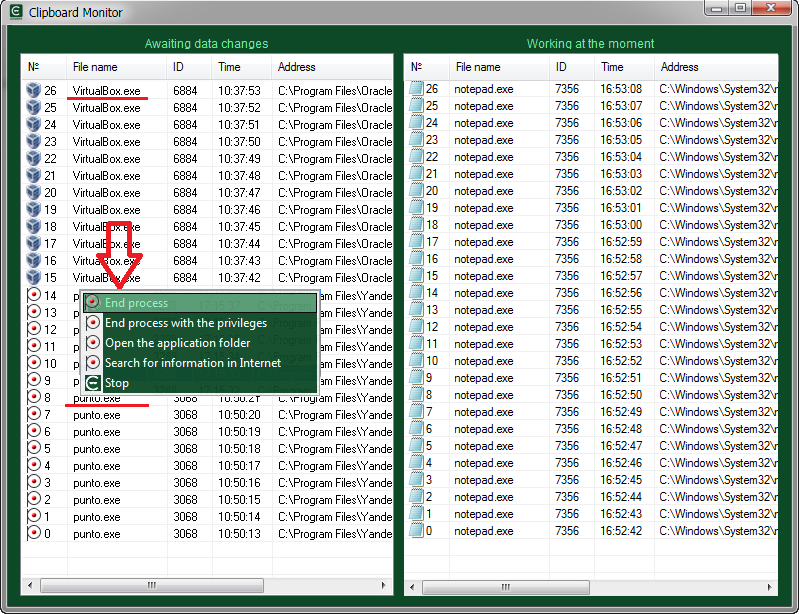
The right list contents applications that are currently working with the clipboard or keep it open. This list allows you to see programs that do not request the clipboard status from the operating system and are not in the queue, but they check the clipboard at regular intervals. They are more difficult to detect. To do this, we will perform a copy operation, because any program that takes contents of the clipboard must open it, duplicate data and close the clipboard.
Usually this operation is instantaneous and it is almost impossible to track it. But at this very moment we will catch the process that interests us. If you copy a large amount of text, the copying will take about 2 seconds or more. Approximately the same time will be needed for the interception operation, and we will have time to detect which program keeps the clipboard open. In the context menu you can select the speed of processing window lists. The more powerful your computer, the higher speed should be set. If you select the speed mode “break v 0.1s“, then the search will stop immediately, after the detection of the application that keeps the clipboard open. The item in the list will be highlighted in red.
Create a large text block in Notepad and copy this data when the clipboard monitor is open in fast processing mode.

After provocative copying, along with the text editor, the data is received by three more programs. The punto.exe process of the Punto Switcher application, the MPK.exe (spyware Mipko which we installed specifically for the test), and the NokiaSuite.exe – process of the data exchange application for NOKIA phones that was installed several years ago and it is not clear why it copies the system clipboard data.
Using this method you can get information about applications that copy your system clipboard into their windows. If they do not have windows in the system, you should use additional COVERT Pro monitors, but we’ll write about this in another article.
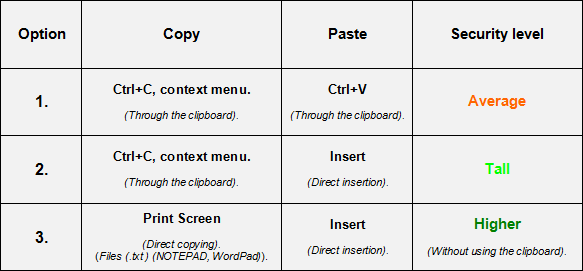
For secure data transfer you should go into secure platform of COVERT Pro, click on the large button in the main window, and select one of the options for copying and pasting.
Copy and paste options inside the platform.
To copy using the context menu, select the text and right-click on it. In the menu that opens, select “Copy”.
In the program, the Print Screen key is programmed for direct copying. This way you can copy from files (.txt) in NOTEPAD and WordPad. The .txt format is the most common format (after .doc) for storing and transmitting text data. Most of the data: nicknames, passwords, links and other private information, users store it in .txt format. If your data for copying is saved in a different format, duplicate it in .txt.
You can paste the copied text with the standard combination Ctrl + V or with the programmed Insert key.
Inside the protection platform you will not be able to use “Paste” from the context menu.
Direct copying of texts in .txt format can be done by pressing the button “Print Screen”. If the copy is successful, the indicator of the internal memory in the main window turns green. If the text is not copied, the indicator will turn or remains white.
Direct insertion of text from the internal memory of the masker can be done to any window with the Insert key. If everything was done correctly, the copied text will appear and the indicator of the internal memory of the masker remains green.

The “Print Screen” and “Insert” buttons allow you to transfer data inside the platform, so you can avoid using the system clipboard.
For more information, read Help by pressing the F1 key while COVERT Pro is running.