Detection and removal of spyware Spyrix Personal Monitor

Developer of the Spyrix Personal Monitor on his web pages declares that his product: «100% undetectable to antivirus software». We decided to check this statement and run antivirus online test. It turned out that this statement is true. Fifty-five anti-virus programs do not define the threat from Spyrix. This means that users who may have this spyware secretly installed, and who rely on anti-virus programs are not protected against identity theft. Therefore, we decided to show – how to identify presence of surveillance.
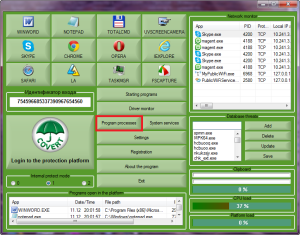
For the detection of hidden spyware Spyrix Personal Monitor, run COVERT and open “System processes”:
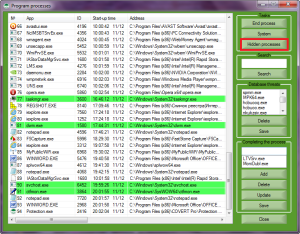
Next, click the “Hidden processes”.
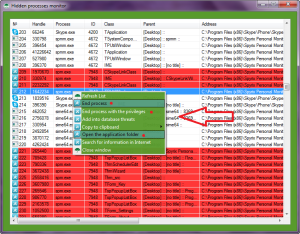
In the “Hidden processes” window, you can see highlighted with red hidden process spm.exe, which belongs to Spyrix. Spyware has been detected. To remove it, you should terminate this process, and then go to the folder of the spyware, using the context menu.
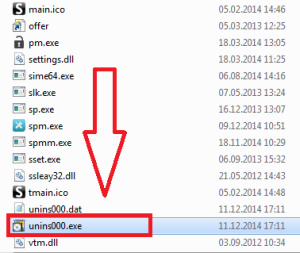
Remove spyware using its uninstaller.
Spyware has been found and removed.
Spyware Spyrix Personal Monitor has extensive functionality for tracking user actions and blocking access to the network. The program gathers information and blocks websites that are in its list. The following screenshot shows the screen that appears when you try to get in to Facebook.
If for any reason you can not remove this tracking tool (for example, it is not your computer, or you are in the workplace), go to the secure platform. In the main window, click the big button “Log in secure platform.” Inside the secure platform, spyware Spyrix will not be able to obtain information about your actions (keyboard input, the data in the clipboard, the image on the screen, websites visited, etc.) and can not block any web pages. You can do whatever you want – open any website, communicate via email or instant messenger. At the same time, the spyware remains installed in the system, but it can not transmit any information to its owner.
Below you can see what spyware has got after user actions in the camoufleur environment.
COVERT provides a unique opportunity to detect surveillance and disguise user actions in the system. In addition, if you install it on a USB-drive, you can use it on all computers to which you have access (at work, at your friends, on a business trip, etc.).
Download COVERT Pro and check FREE of charge your computer for spyware and rootkits, which were not detected by an antivirus.