Invisible spy Micro Keylogger

This spyware belongs to one of the most dangerous types of monitoring programs. They are very hard to detect because they do not have any active processes, services and does not use the standard methods. Their activity is conducted through the DLLs that are loaded by system process rundll32.
(DLL – Dynamic Link Library, is a type of file that contains instructions that other programs can call upon to do certain things. This way, multiple programs can share the abilities programmed into a single file.)
In a matter of seconds all collected information spyware sends to a special server or email address. It also uses the system process explorer.exe.
(explorer.exe – it is an executable file of Windows Explorer)
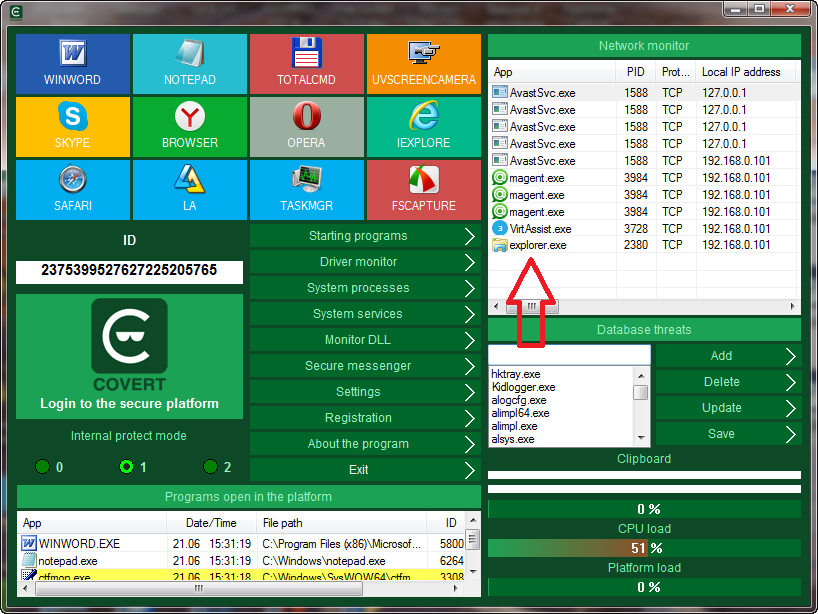
Checking the status of the system using ‘System process monitor’ does not detect the presence of any strange processes. There are no suspicious programs in startup. Given the fact that Micro Keylogger is not considered dangerous by the vast majority of antivirus programs, you can come to the mistaken conclusion that the computer is clean and there are no installed spyware on it. Unfortunately, many people think so. But you should check loaded DLLs.
This can be done by special function of COVERT Pro – Monitor DLL. Viewing the status of the operating system by other monitors (drivers, processes and services) does not provide information that could arouse suspicion. If you use COVERT Pro for PC, which needs administrator rights, you should disable user account control (UAC) in Windows. Otherwise you will not be able to see all the spyware libraries as spies without administrator rights can’t connect to programs. If you have COVERT Pro USB version, you can run it without administrator rights and you may not disable the UAC.
(UAC is a security feature of Windows which helps prevent unauthorized changes to your computer).
UAC can be disabled in the context menu that appears by right-clicking on the frame of the window. After examining the list of libraries you can turn on UAC in the same way.
Now restart your computer, run COVERT Pro and open Monitor DLL.
File core32_3.dll is highlighted in red in the list of loaded libraries. This DLL belongs to spyware Micro Keylogger. Only now we found out that our computer has a program for tracking user’s activity. The name and path of the folder where spyware was installed C:\Windows\security\Syslogs.
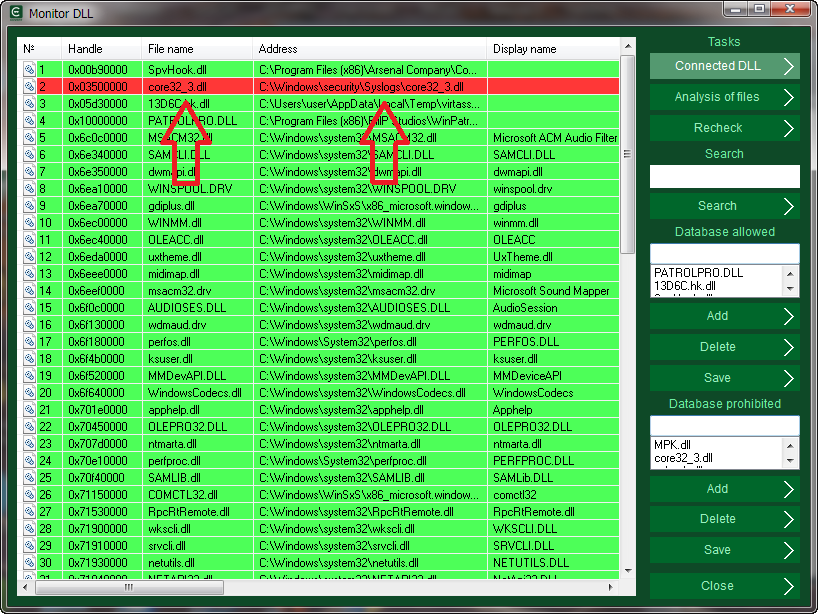
Micro Keylogger was detected. Let’s see how to remove it now. Click with the right mouse button on the red line and select disable in the context menu.
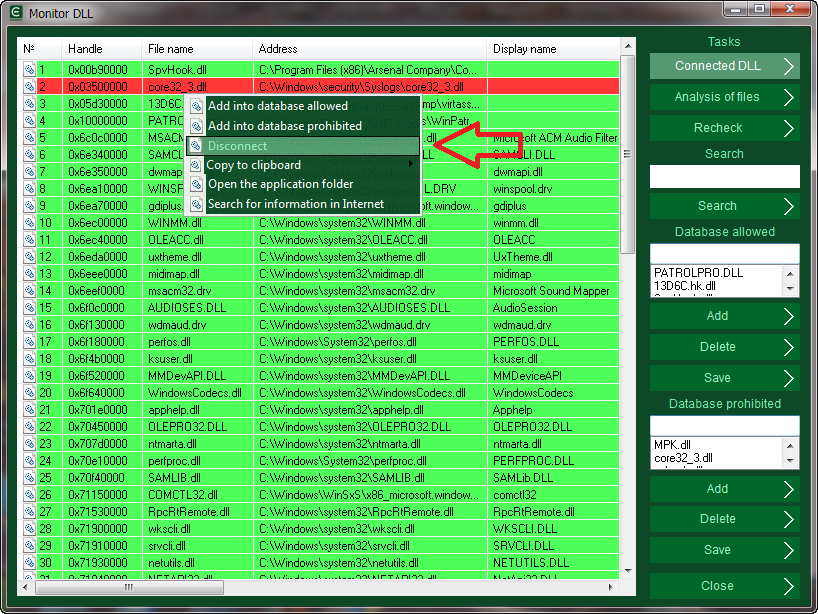
Then confirm your action and restart computer to complete this operation.
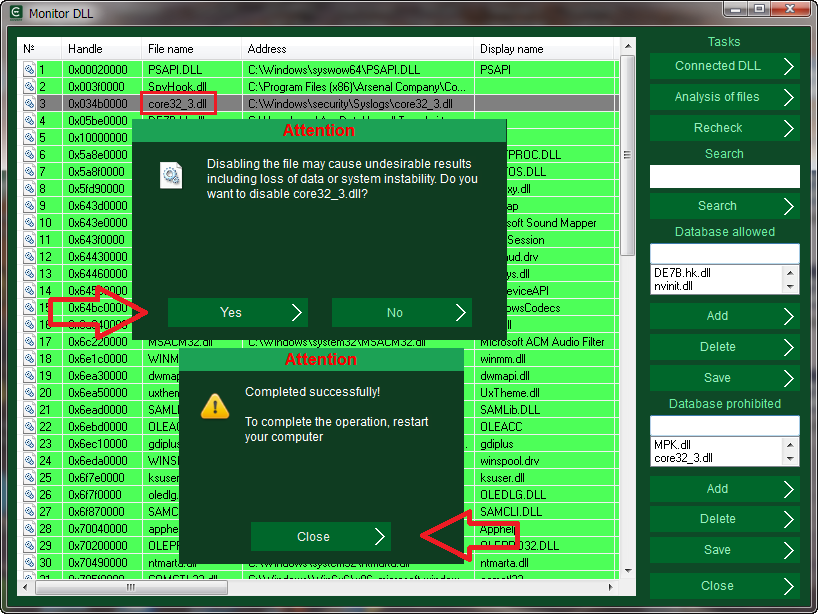
After restarting your computer, Spyware Micro Keylogger will no longer work on it.
You should delete the folder with files of tracking program – C:\Windows\security\Syslogs.
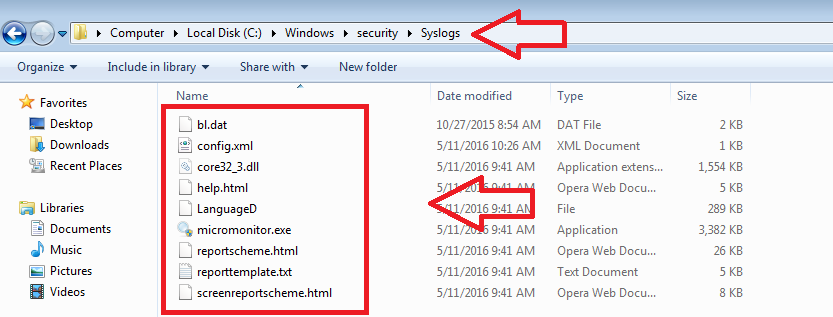
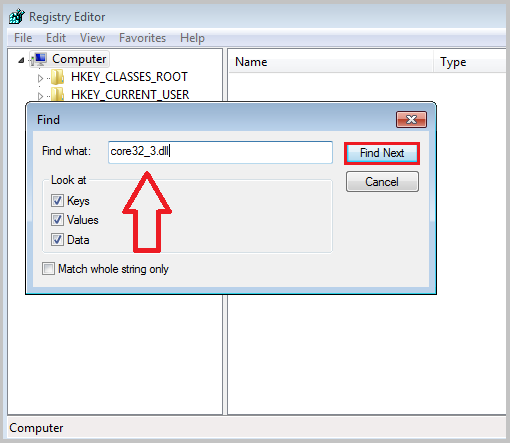
If you see error message about core32_3.dll, then you need to open the registry, search all the parameters that contain the name of the spyware library core32_3.dll and delete them.
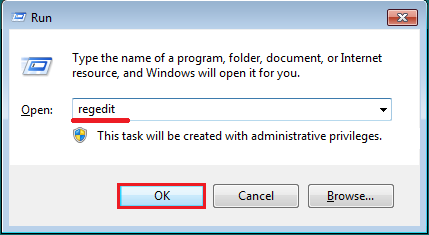
To do this, press on the keyboard Win + R, enter regedit and press Ok.
To disguise your actions from Micro Keylogger, without removing it from your computer it will be enough to enter secure platform by clicking on the large button with the logo and the inscription “Login to the secure platform.”
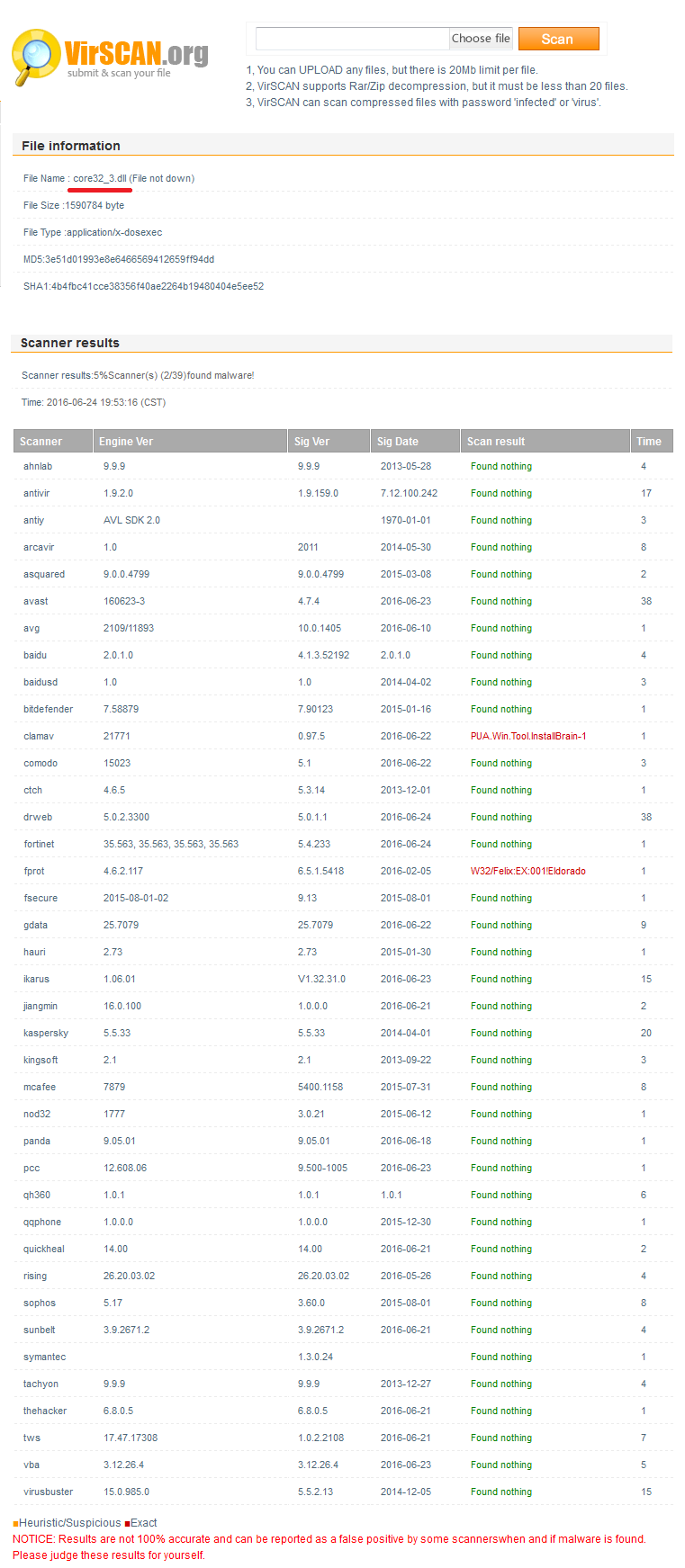
And as always, in the end of our article we publish the screenshot for people who believe that antiviruses on their computers can protect against all threats related to the theft of confidential information.
We checked (and you can do it too) file core32_3.dll on one of the most popular online services using 39 antivirus programs. Only two of them (5%) were able to find a threat in this spyware.
Download COVERT Pro and check FREE of charge your computer for spyware and rootkits, which were not detected by an antivirus.